
Policy-Makers Navigating the Limits of Data: Understanding the Trade-offs of Decontextualization
The complexities of data usage in decision-making as we delve into C. Thi Nguyen's insights on the inherent limitations of data, the challenges of decontextualization, and the importance of balancing quantitative and qualitative methods for a nuanced understanding.

FCC Unveils Groundbreaking Framework for Supplemental Coverage from Space
The FCC has established new guidelines to create the world's first Supplemental Coverage from Space framework, which will revolutionize connectivity by employing satellite technology to expand wireless network reach to rural places, providing continuous smartphone access.
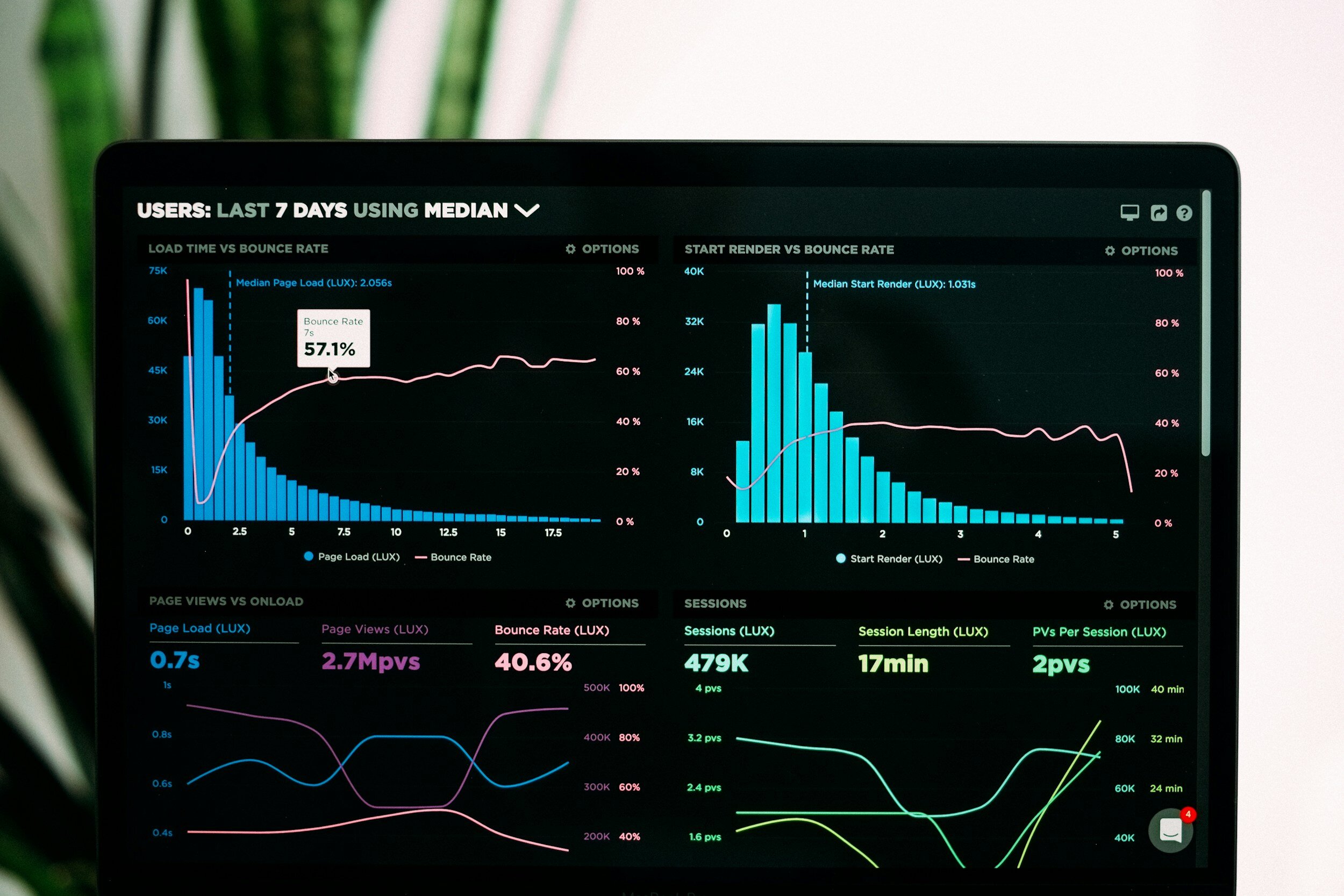
Enhancing IT Investment and Performance with World Class Alignment Metrics in the Navy
The Department of the Navy is revolutionizing IT investment and performance evaluation with World Class Alignment Metrics (WAM). Learn about the focus on data-driven decision-making, outcome-driven metrics, and the strategic implementation of WAM to improve mission outcomes and operational resilience.

Strengthening Domestic Sourcing: A New Direction in Federal Procurement
Learn how the United States government is reviving domestic manufacturing through a pilot initiative that improves price preferences for important items in federal procurements. Learn about attempts to enhance domestic supply chains and the consequences for businesses and the economy.
Enhancing Cybersecurity in the Defense Industrial Base: A Closer Look at DoD's Final Rule on Eligibility Criteria for the voluntary DIB
The latest updates and final rule making to the Department of Defense's Defense Industrial Base Cybersecurity Program. Learn about expanded eligibility criteria, changes to information sharing, and the impact on defense contractors. Stay informed about the future of cybersecurity in the defense sector.

The Future of Secure Cloud Business Applications: A Guide to Hybrid Identity Solutions
CISA's guidance on Secure Cloud Business Applications, focusing on Hybrid Identity Solutions for modernizing identity management in the cloud era. Learn about transitioning to cloud-based, passwordless authentication, implementing multifactor authentication (MFA), and leveraging single sign-on (SSO) for enhanced security and user experience in federal agencies and organizations.

Tumultuous Terrain: An Overview of the 2024 Annual Threat Assessment
The 2024 Annual Threat Assessment by the U.S. Intelligence Community highlights global security challenges, including the actions of state actors like China, Russia, Iran, and North Korea, regional conflicts, transnational issues, and the impact of disruptive technologies and environmental changes on national security.

Unveiling the Future of Defense Spending: The Investment Strategy for the Office of Strategic Capital (OSC for Fiscal Year 2024
The U.S. Department of Defense's strategic investment blueprint through the Office of Strategic Capital (OSC). Focused on national security, the OSC aims to attract private capital to critical technologies, strengthening supply chains and maintaining the U.S.'s technological edge.

The Future of Open Source Intelligence: The IC OSINT Strategy 2024-2026
The key highlights of the U.S. Intelligence Community's Open Source Intelligence (OSINT) Strategy for 2024-2026. Explore how the IC plans to harness the power of publicly available information to enhance national security, innovate collection methods, and develop a skilled workforce for the future. Learn about the strategic focus areas and the importance of partnerships in advancing OSINT capabilities.
Strengthening Cloud Security: NSA's Top Ten Mitigation Strategies
Discover essential cloud security insights with NSA's Top Ten Cloud Security Mitigation Strategies. Learn how to safeguard your data and infrastructure against cyber threats with best practices for identity management, encryption, and more in our latest blog post.

Understanding the 2023 FBI Internet Crime Report: Insights and Trends
The 2023 FBI Internet Crime Report highlights the rise in cybercrime, with a record 880,418 complaints and losses exceeding $12.5 billion. Key trends include investment fraud, business email compromise, and ransomware attacks. The report emphasizes the crucial role of the IC3 in combating cyber threats and the importance of reporting incidents to enhance cybersecurity efforts.

Advancing Zero Trust Maturity in Network and Environment Security
Read about the importance of Zero Trust maturity in network and environment security with the NSA's guidance. Learn about implementing segmentation, access controls, and software-defined networking to enhance your organization's defense-in-depth posture and protect against lateral movement by malicious actors. Essential reading for National Security Systems, the Department of Defense, and the Defense Industrial Base.

A New Approach to Defense Resourcing: The Commission on PPBE Reform's Recommendations for Change
The Commission on PPBE Reform recommends a new approach to defense resourcing to maintain American security. It addresses challenges from strategic adversaries and rapid technological innovation, proposing changes to align budgets with strategy, foster innovation, and strengthen relationships between DoD and Congress.

Challenges and Strategies in Recruiting for 1102 Contracting Positions in Federal Government
The intricacies of recruiting for 1102 contracting positions in the federal government. Discover the hurdles like compensation, complex hiring processes, and workplace culture, and learn about strategies such as improving pay, streamlining recruitment, and investing in training to attract and retain skilled professionals in this vital field

SBA Enhances Lender Match Platform: A Boon for Small Businesses Seeking Capital
How the enhanced SBA Lender Match platform simplifies access to capital for small businesses, featuring a mobile-first interface, lender comparison, and fraud screening.

Enhancing Cyber-Physical Resilience: A Call to Action by PCAST
The President's Council of Advisors on Science and Technology (PCAST) highlights the urgent need for a collaborative effort to fortify the resilience of critical infrastructure against threats. Emphasizing the importance of public-private partnerships, the report recommends establishing performance goals, bolstering research, and ensuring greater accountability in industry leadership to safeguard essential services and adapt to the challenges of the digital era.

Executive Order on Protecting Americans' Data from Foreign Threats
On February 28, 2024, President Biden signed an Executive Order to safeguard Americans' sensitive personal data and U.S. government-related data from access by countries of concern. This order expands a national emergency to address security risks posed by foreign access to bulk data. It outlines policies to restrict such access when it poses a national security risk, while supporting open data flows. The order details prohibited transactions, measures to protect sensitive data, and steps to assess risks from prior data transfers

Transforming for the Future: The U.S. Army's Force Structure and Recruiting Revolution
Explore the U.S. Army's transformative journey as it adapts to modern warfare by reshaping its force structure and revolutionizing its recruiting strategies. Discover how the Army is preparing for large-scale combat operations, integrating new capabilities, and ensuring readiness in a rapidly evolving security landscape
Enhancing Fraud Risk Management in DOD Contracting Through Data Analytics
Explore how the Department of Defense can improve its fraud risk management in contracting by incorporating data analytics, as recommended by the Government Accountability Office. Learn about the challenges and recommendations for better fraud detection and prevention in DOD procurement processes.
Navigating Cybersecurity in the Digital Age: Insights from NIST CSF 2.0
How the NIST Cybersecurity Framework (CSF) 2.0 guides organizations in enhancing their cybersecurity posture. Learn about its adaptable structure, including Functions, Categories, and the use of Profiles and Tiers, making it essential for managing cybersecurity risks in today's digital world.